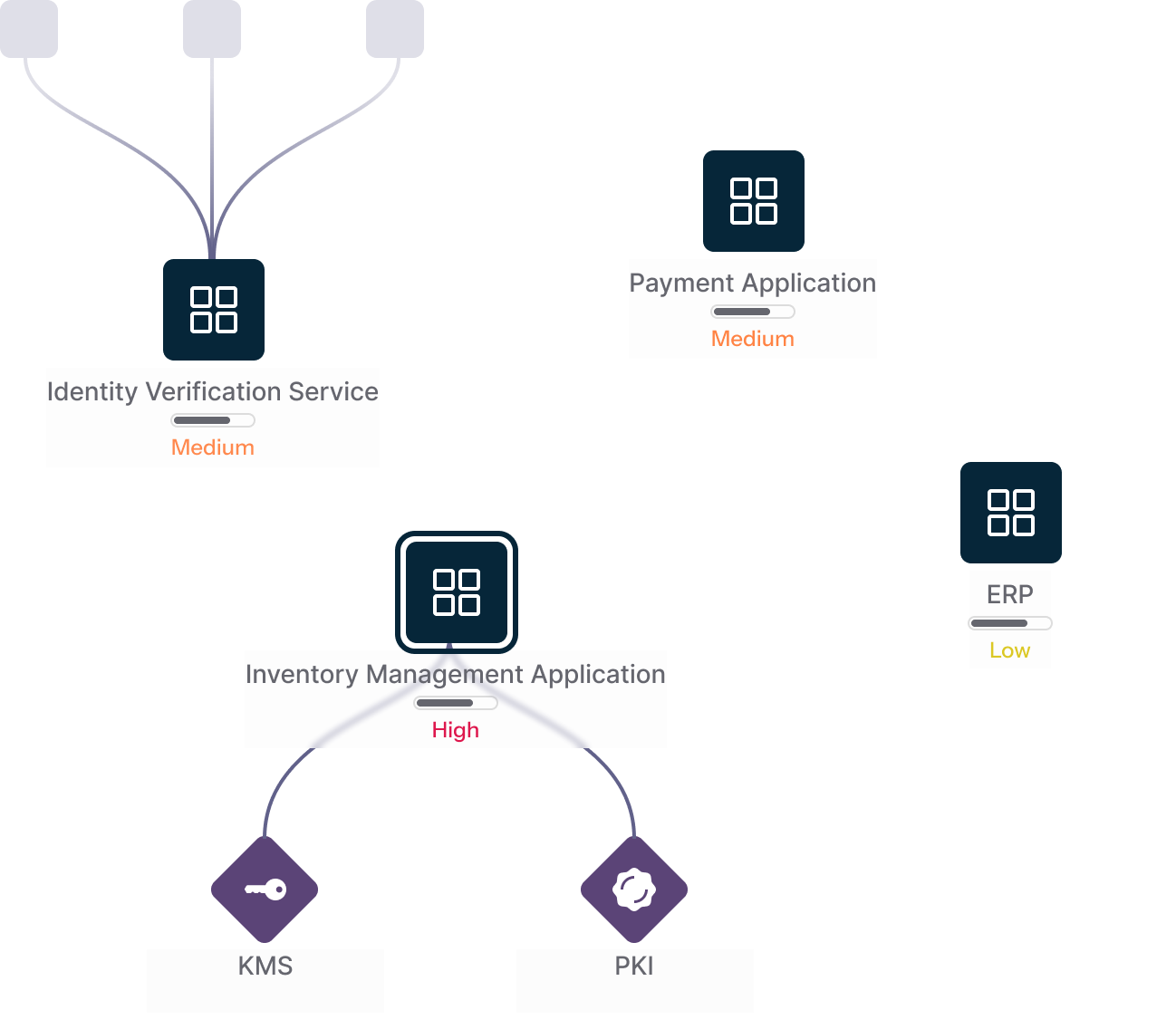
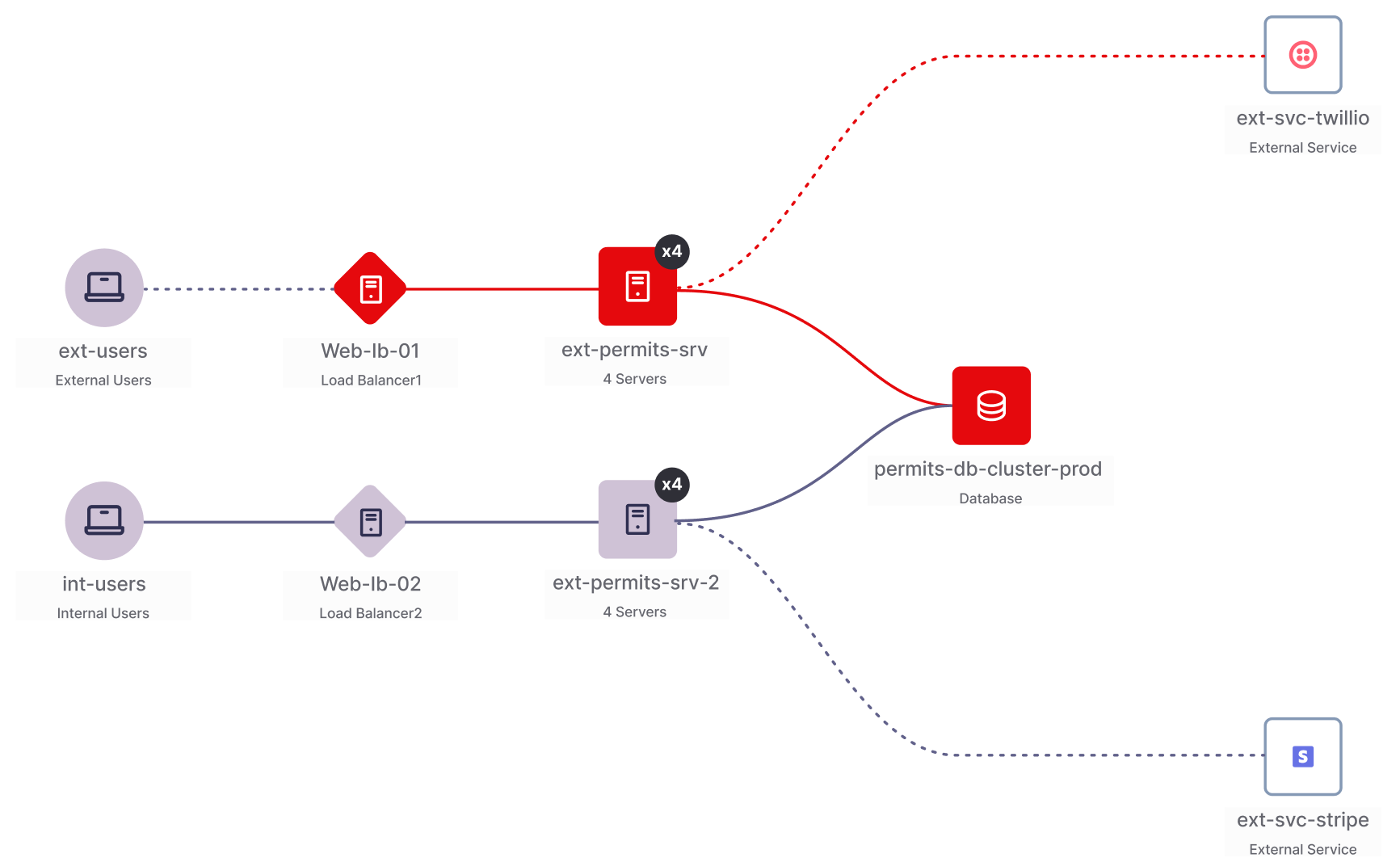
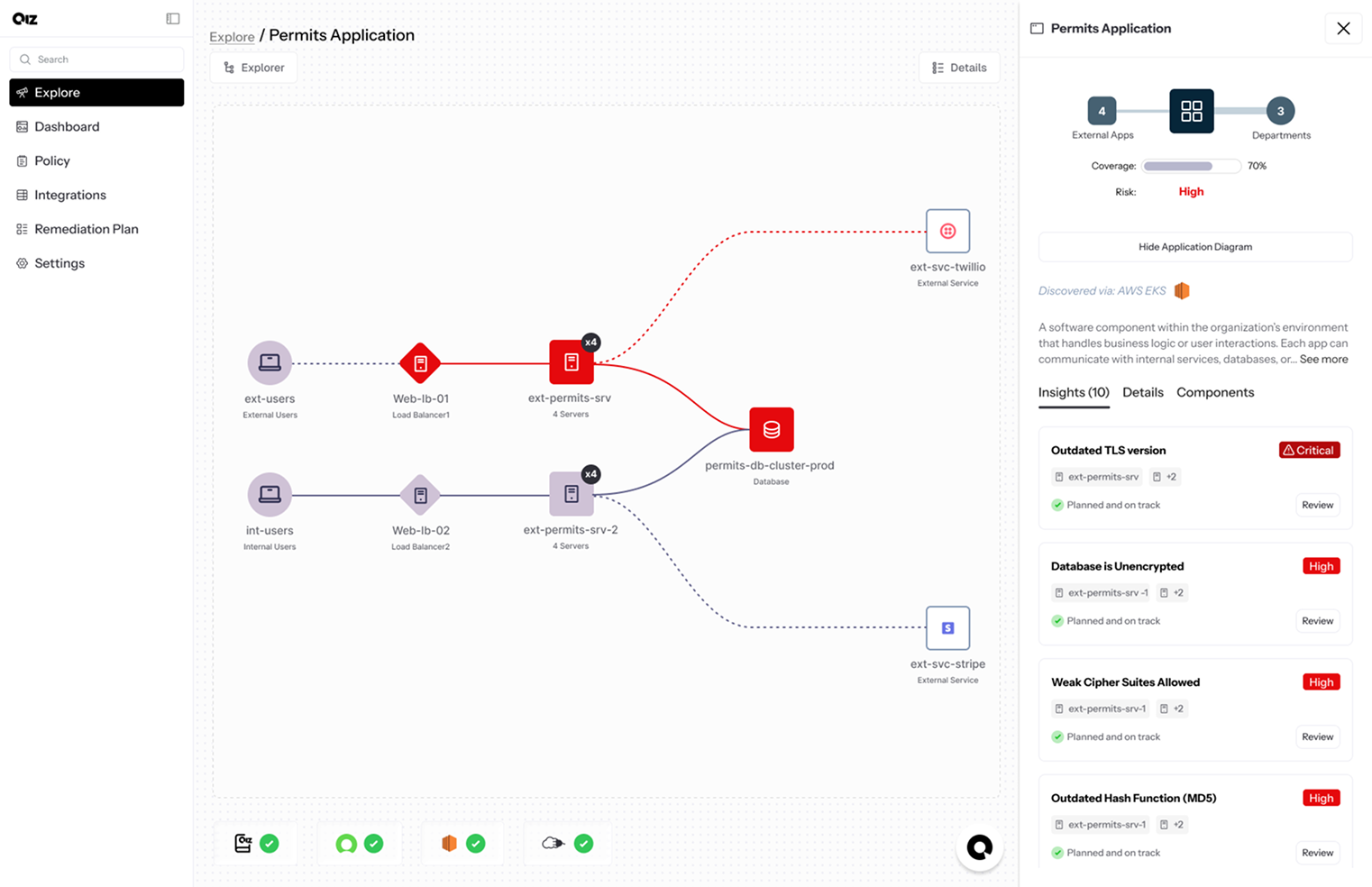
Exposing Crypto Risks in Motion and at Rest
Every application hides its own risks, data in transit between systems, and data at rest inside databases and storage. By mapping all dimensions, QIZ shows where outdated protocols, weak encryption, or any control violation exposes your applications.